This just means that your wife needs to update her account settings.
There is a very small chance that something could go wrong while doing the update, so out of an abundance of caution (since breaking your wife’s account could be a problem), you should export a password-protected backup copy of her vault contents and take some additional precautions before you start.
Creating an Export:
- Log in to your wife’s account on the Web Vault (vault.bitwarden.com).
- Click on Tools in the top menu bar.
- Click on Export Vault in the left-hand navigation menu.
- In the dropdown menu under File Format, select the option .json (Encrypted).
- You will now see two options for Export Type: select Password-Protected (it is very important that you don’t select Account-Restricted).
- Choose a strong password for the backup (use the Bitwarden Password Generator if you like), and enter it into the input fields File password and Confirm file password. Write down this password in a safe location, so that you don’t lose it!
- Click Confirm Format.
- When prompted (in a window titled Confirm Vault Export), enter the Bitwarden Master Password (not your backup password).
- Click Export Vault button. You should see a green alert box in the upper right corner of your browser window, with the message “Vault data exported.”
- Go to your Downloads folder, and look for a file named something like
bitwarden_encrypted_export_20230612204532.json. Move this file to any location where you will be able to access it later. The file is encrypted, so you do not have to worry about hiding the file.
In addition, if you have file attachments in your vault, locate these by typing the following expression in the vault search bar:
>attachments:*
Then, download each attachment (as file attachments are not included in the vault export), and make a note of which vault item each file was attached to. If you are concerned about the security of saving these files in decrypted form on your computer, you will need to take special measures (which I won’t detail here, unless you ask).
Finally, if your wife uses the Bitwarden Send feature, then take any necessary actions to preserve or re-create any currently active Sends (as Sends are not included in vault exports and would be lost should something happen to the account).
Additional Precautions:
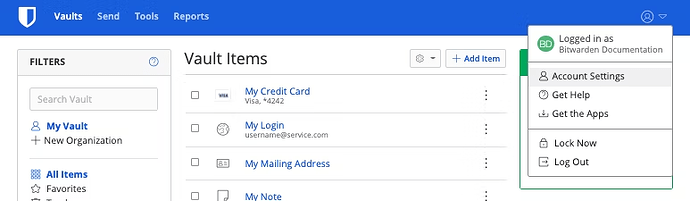
In case you don’t already have it, you should get your two-step login recovery code. While still logged in to the web vault, click the profile avatar in the upper right corner, and select “Account Settings” from the dropdown menu:
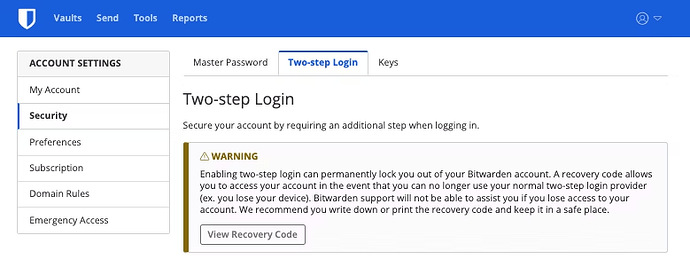
In the Account Settings section, select Security in the left-hand navigation menu, and then click the top tab that is labeled “Two-step Login”:
In the Warning box, click the View Recovery Code button, and enter your wife’s Master Password when prompted. This will display a 32-character code, which you should print out or write down in a secure location (e.g., your Bitwarden Emergency Sheet).
While you’re on the “Two-step Login” tab, look through the list of “Providers”, and ensure that you see a green check mark (  ) on at least one of the listed provider options. If not, you’ll have to have a talk with your wife about the importance of two-factor authentication.
) on at least one of the listed provider options. If not, you’ll have to have a talk with your wife about the importance of two-factor authentication.
Updating the KDF Settings:
Having taken the above precautions, you’re now ready to make the KDF update that will address the “Low KDF Iterations” warning.
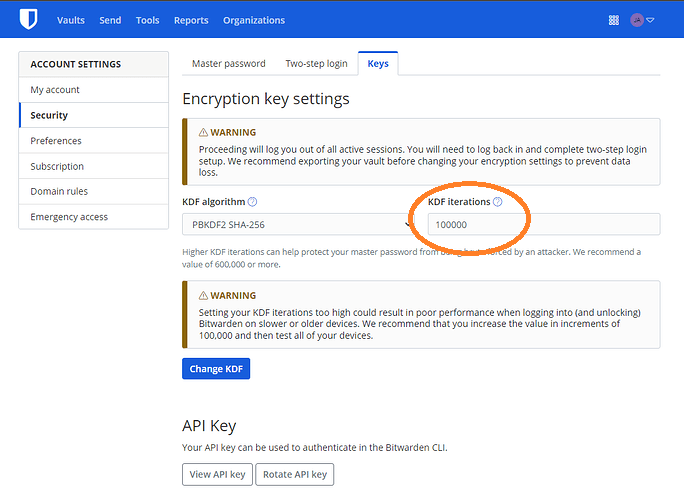
While still on the Security page of the Account Settings section, click the top tab that is labeled “Keys”. This will take you to a screen titled “Encryption Key Settings”.
In the “Encryption Key Settings” screen, change the value of “KDF Iterations” from 100000 to 600000, and then click the Change KDF button:
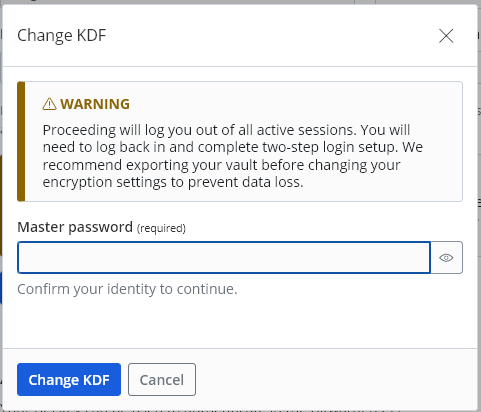
You will be prompted for the master password at this point, after which you can click the Change KDF button in this final prompt:
 Important: Please warn your wife that she will be logged out of all of her Bitwarden apps when you complete this step. To resume using Bitwarden, she will need to log back in to her account on all Bitwarden apps on all of her devices.
Important: Please warn your wife that she will be logged out of all of her Bitwarden apps when you complete this step. To resume using Bitwarden, she will need to log back in to her account on all Bitwarden apps on all of her devices.
Note: The Warning box on the final prompt (shown in the screen shot above) includes the statement “You will need to log back in and complete two-step login setup.” This statement is incorrect, and can be disregarded. What that sentence should say is something like “You will need to log back in (and complete two-step login, if set up)” (see discussion here). Bitwarden plans to change the sentence to “You will need to log back in and complete two-step login, if any.”
![]() So:
So: