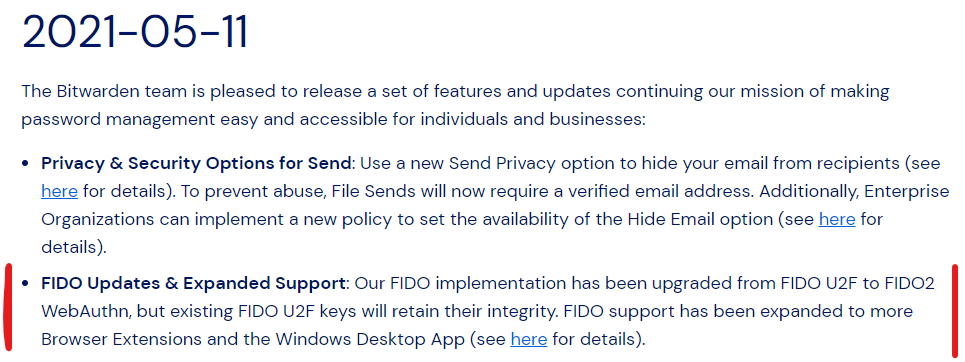
@Micah_Edelblut
As others have already noted, we “jump starters” will need some instruction on how to use the tool. When I used the tool to register one of my Yubikeys, it created a non-discoverable credential, and produced the output shown below (in slightly redacted form). What do I learn from this JSON salad?
navigator.credentials.create() argument:
{
"publicKey": {
"attestation": "direct",
"authenticatorSelection": {
"requireResidentKey": false,
"residentKey": "discouraged",
"userVerification": "discouraged"
},
"challenge": "redacted",
"excludeCredentials": [],
"pubKeyCredParams": [
{
"alg": -7,
"type": "public-key"
},
{
"alg": -257,
"type": "public-key"
}
],
"rp": {
"id": "demo.yubico.com",
"name": "Yubico Demo"
},
"timeout": 600000,
"user": {
"displayName": "Yubico demo user",
"id": "redacted",
"name": "Yubico demo user"
}
}
}
navigator.credentials.create() response:
{
"id": "redacted",
"response": {
"attestationObject": "redacted",
"clientDataJSON": "redacted",
"transports": [
"nfc",
"usb"
],
"publicKeyAlgorithm": -7,
"publicKey": "redacted"
},
"authenticatorAttachment": "cross-platform",
"clientExtensionResults": {}
}
Parsed clientDataJSON response:
{
"type": "webauthn.create",
"challenge": "redacted",
"origin": "https://demo.yubico.com",
"crossOrigin": false
}
Response from the Relying Party:
{
"success": true,
"attestationObject": {
"attStmt": {
"alg": -7,
"sig": "Redacted",
"x5c": [
"Redacted"
]
},
"authData": {
"credentialData": {
"aaguid": "redacted",
"credentialId": "redacted",
"publicKey": {
"1": 2,
"3": -7,
"-1": 1,
"-2": "redacted",
"-3": "redacted"
}
},
"flags": {
"AT": true,
"BE": false,
"BS": false,
"ED": false,
"UP": true,
"UV": true,
"value": 69
},
"rpIdHash": "redacted",
"signatureCounter": 2
},
"fmt": "packed"
},
"clientData": "redacted",
"device": {
"mds": {
"certifications": [
"FIDO_CERTIFIED_L1"
]
},
"mdsUnavailable": false,
"names": [
"Security Key NFC by Yubico",
"Security Key C NFC by Yubico"
],
"type": "skynfc-skycnfc",
"yubicoFirmwareVersion": "5.4.3"
}
}