I understand that the master password hash is used to encrypt and decrypt my password vault. The hash is generated on client side and validated on server side. However what if my master passwords hash itself is leaked? Then is there is a possibility that a bad actor can decrypt my password vault using the hash?
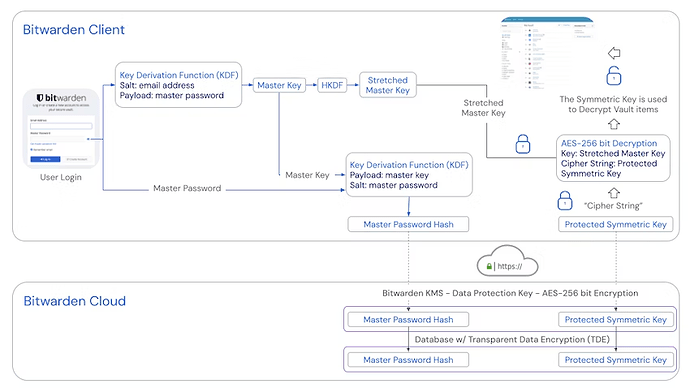
The master password is run through a KDF (pbkdf2 or argon2) to result in your master key. This master key is used to decrypt the encrypted “user key” which is then used to decrypt your vault entries.
To authenticate to the server, the master key is hashed, and sent to the server as the “masterpasswordhash”. Because the hash is one-way, the hash being leaked does not help with decrypting your vault.
hmm ok consider this scenario:
Vault data is leaked and my master password hash, so now why can’t the hacker decrypt the password vault ? What is stopping him? he has everything he needs.
First, the hash has been encrypted before it is stored on Bitwarden’s servers, so an attacker who has compromised Bitwarden’s cloud database would independently have to mount a successful attack against Bitwarden’s Key Management System (KMS) before they can access the actual hash.
Second, the hash cannot be used to decrypt the password vault, it is only used for authentication (i.e., to allow Bitwarden’s servers to confirm that you are the rightful owner of your vault).
Decryption requires the account encryption key, which requires the stretched master key, which requires the master key, which ultimately requires your master password. Note that the master password hash is not used anywhere in the decryption process.
This diagram from Bitwarden’s Security Whitepaper may help:
Thank you for the good explanation