And now the original problem has recurred.
The BitWarden version I have is -
Version 2025.8.0
SDK ‘main (29c6158)’
Shell 36.4.0
Renderer 136.0.7103.149
Node 22.15.1
Architecture x64
The o/s is - Windows 11 Pro Version 24H2, Build 26100.4946
The Hello login window pops-up automatically when I start my PC and I can use it to login to my Windows account.
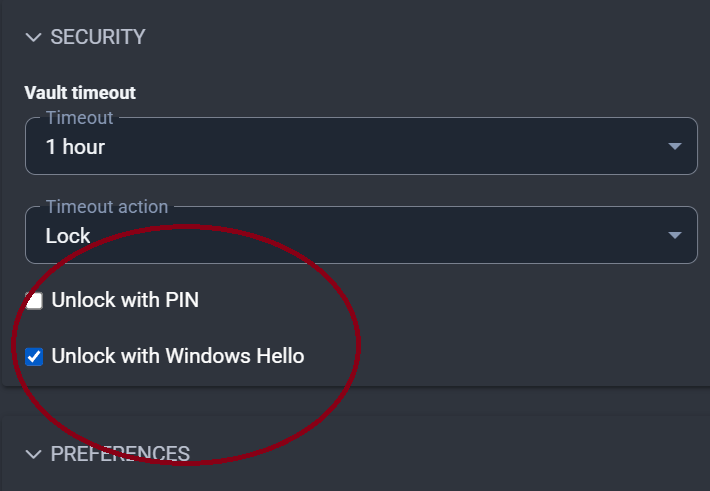
Bitwarden is set to auto-start (which it does) and I have checked the “Unlock with Windows Hello” box in Settings > Security. [The box “Ask for Windows Hello on launch” which used to be part of the Bitwarden Settings is no longer present (when did that disappear?)]
BitWarden does launch automatically but - and this is a BIG change - not only does it not launch the Hello pop-up, the “Unlock with Windows Hello” button is now grayed out and disabled. The only way in is to use my master password.
But then, after logging in to the main desktop app, when I unlock my browser extension for the first time, it DOES launch the Windows Hello login window, and I can use fingerprint recognition to open the extension.
Very strange. Does anyone consider that a complete uninstall, scrub registry, and reinstall afresh would have any benefit? That’s the level I’m thinking of now.