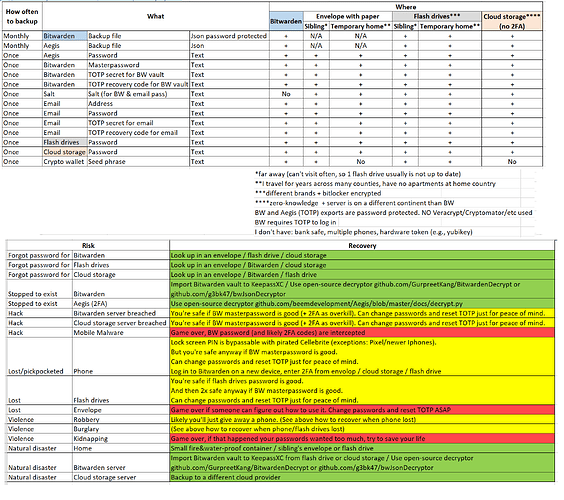
Welcome. The items you highlighted in RED would be the same for any software. If you are using a pwned machine the interceptor would have control, nothing new. Also, if you are using an envelope along with two factor authentication the “bad folks” would need access to your YubiKey, or other method used too.