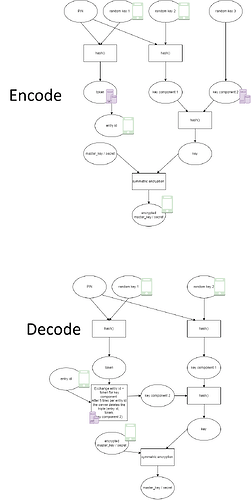
…by introducing a sever stored key part. The whole idea is to let the sever check the 5 tries limit and deleting it’s part of the encryption key if all tries where used or a timeout (e.g. 1 day) is reached.
I’m currently not a bitwarden user, but investigating if I want to change. I came a lot of posts discussing the problem that a pin encrypted master key could be extracted on the client side and be brute forced (due to low entropy). Then an idea came to my mind: why not introduce a server side component? If this idea was already discussed somewhere where I didn’t find it - I’m sorry in advance.
Sorry for the quality - I had to put the two pictures together (as I’m not allowed to post more than one ![]() )
)
The icons symbolize where the the keys are stored (client or server).
Advantages:
- brutforce the encrypted master key is not longer possible (without having control over the server)
- the server will only provide is key-part if the client can prove it is knowing the pin
- the server does not get any information about the master-key nor the pin
Disadvantages:
- the server needs to be reachable for pin unlock (allow the user to turn this off if he is offline often)
- more complex logic required
What do you thing about this idea?