Expanding on this idea is the expiration date, that would automatically generate an expiration date note (showing all upcoming expiration dates) and (optional) expiration date alerts.
In my opinion an expiration date would be part of an item template discussed elsewhere. But of course the field type would be the same.
Agreed, 1password provides expiration dates for passports and driver’s licenses out of the box, and then provides a useful report for “things about to expire.”
Feature name
-name/concept of the feature being requested
- Custom Field -> Add Type:Date/Time, selective + manual fill in + GMT time zone
- Notification (1 or 2 or 3 or specify the reminder) in the centralized like Dashboard to list those nearing expiration items
Feature function
-
What will this feature do differently?
the purpose is to notify for those items nearing for expiration.
for example, my VISA, Credit Card, Apps Subscription, Driving License is about to near expire -
What benefits will this feature bring?
Among hundreds of items, there will be a centralized dashboard or field to take a quick glace look and sort them to make things more effective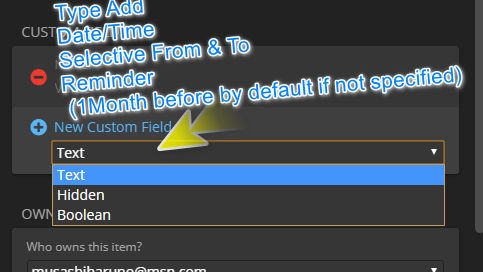
There already is a feature request for custom field type ‘date’
Having an expiration date to be monitored would require a dedicated field like in KeePass. That would allow to create an extra health report or other monitoring function. Nice idea.
Fully agree: date field would be very welcome.
Fine to split the request in two, add custom field date soon and add the “notification” functionality later.
Having a date field can have multiple purposes: expiration date, date created, date of purchase, DOB, etc. Not for all of them a reminder is wanted/needed.
For the custom date field: full date but preferably also: month/year (e.g. for cc expiration date)
Related: for the 1Password import, currently the date fields are imported as Epoch timestamps (e.g. -23395600 [before 1970] and 1434728860). That is not very useful. Would be great if they can be imported as date strings e.g. “March 8, 2021” or “2020-03-08”.
Would it be possible to split this request again?
This so it is possible to vote on (and build) them separately:
- date field (full date and mm/yy) + correct 1Password import
- date field expiration monitoring
The first one has a much higher priority for me than the 2nd.
Whenever I need to provide my passport number (e.g. for a flight), I also have to provide the passport’s expiration date. At the very least, it would be nice if I didn’t have to store that in a basic text field.
Bumping this as I agree this would be a very beneficial feature to have. Knowing a password is expired BEFORE I try to use it would be nice as I could go ahead and generate a new password to use OR know that I need to change it BEFORE it expires (as some systems are not very friendly when a password has been allowed to expire).
Hey
I just used this feature (as a plugin) in KeePass and think this would also suit bitwarden.
Corporate accounts nowadays have to reset their password every 3-12 Months. Would be great if bitwarden gives me a notification every X months repeatedly so I don’t forget it.
Maybe add it to the advanced features of the login fields. But selecting the amount of Days/Weeks/Months or so to get a notification to change the password would be nice.
If you are unsure on how I imaginate this feature to be, check out this KeePass plugin.
Regards
A must have for promoting the good practice of rotating passwords every X time.
the good practice of rotating passwords every X time.
No, that’s not a “good practice”, it’s an evil that’s forced on us from the top.
Could you elaborate on this?
Back then when it was implemented in the mid 80’s no one really knew anything about IT-security, the only password requirement was the length of 8 characters and it was “the password”, singular, you only had one.
Back then, some people thought it would be a good idea to change it regularly so the relevant US gov. agency published that recommendation.
At least since 2000, it’s been known that regular password changes are decreasing the security.
Even the government agencies who were “recommending” that, took these “recommendations” back years ago (2018 in the US and 2019 in Europe).
But some big, evil enterprises like Microsoft and others are still forcing it from the top.
No rule without exception: If a code or password is used by several people, regular password/code changes may be a good idea, because workers change departments or employers and often no one thinks of changing the password/code after that.
My scenario is the following:
I have passwords for thousands of sites and all (most) of them are random passwords larger than 8 characters.
Now, during my workflow, some of these passwords could accidentally get exposed, for example, by being placed in known local configuration files that could get exfiltrated by malware (you cannot be always 100% sure for all the software you install).
On the other hand, from time to time I end up sharing some passwords (e.g. Netflix, Wi-Fi or even bank accounts) and after some time I simply forget that I’ve shared those passwords and their usage could evolve to an use I don’t expect and don’t want like them being shared with other people or they could get simply exposed because of a lack of care (or ability) of the people I’ve shared them with.
Now, if I would have a self-configured reminder that I have to change certain passwords every, let’s say 3 or 6 months, the impact of the previous problems could be alleviated and I could have more peace of mind.
I end up sharing some passwords (e.g. Netflix, Wi-Fi or even bank accounts) and after some time I simply forget that I’ve shared those passwords and their usage could evolve to an use I don’t expect and don’t want like them being shared with other people or they could get simply exposed because of a lack of care (or ability) of the people I’ve shared them with.
That’s the exception I mentioned.
Anyone who reads his response, this is accurate (as a enterprise sec analyst). Its old knowledge that is no longer applicable.
Passwords should be rotated really only if compromise is suspected. It’s otherwise a waste of time or unnecessary risk.
If you won’t take no for an answer (or have EXTREME security reqs), I recommend a yearly change, max.
It would be great if each secret had an expiry date against it. Many secrets have limited validity, after which they cannot be used. Expiry dates could be used to show secrets that will soon expire, as well as providing a way to notify users to refresh them before they do.
Even if they don’t actually expiry, having a date would also provide a reminder to periodically update the secret.
With the rapid development of AI Large language models, a series of security problems have also followed, and it is hoped that Bitwarden can provide users with password rotation reminder function, which can remind users to rotate passwords at least 14 days apart.
Hi @AkarinLiu - Thanks for sharing. This item is being watched by the team for consideration in a future release.
At the same time NIST actually recommends NOT changing passwords regularly unless they are suspected of being compromised.