I’ve recently seen Session’s 13 words long recovery phrases, They use that 13 words as a master key, It feels like a real uncrackable master password and I’m actually considering to pick one of the Session’s 13 words passphrase and use it for my master password right now, Should I use it? What do you guys think? I need opinions on that, I want to use a very very strong future proof passphrase as a master password still I can’t decide how many words I should use.
If you can remember a passphrase consisting of 13 random words, and you don’t mind entering it every time it’s requested, then go ahead. It’s really overkill, though. A passphrase of at least 20 letters consisting of 4 random words would be more than adequate in my opinion. Couple that with two-factor authentication and you’re in a very good position.
thank you for the answer, maybe I’ll use 10 words, I’ve heard 128 bits of entropy is future proof very strong password, Does 10 words passphrase have 128+ bits of entropy?
Check it out yourself at: Password Entropy Calculator
Depends on the length of the words. Purely using lower case letters, 27-28 would be enough for 128 bits of entropy, not that I think you need that many. Bear in mind, the words need to be truly random in order for a passphrase to be effective.
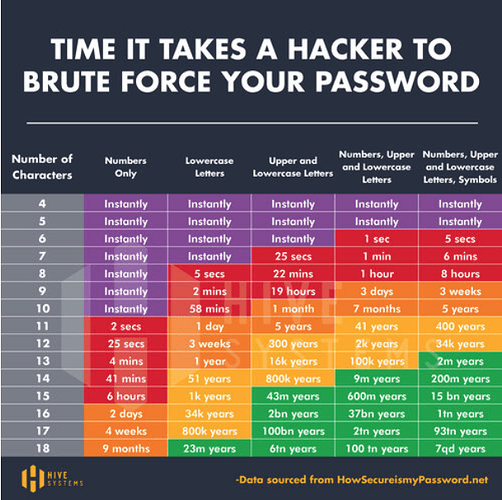
In addition to the good advice @Peter_H has provided above, you might consider the time it takes to crack a password instead of entropy, because entropy is a bit of an abstract metric whereas time in days or years or centuries is something we can all easily relate to:
source: The 2025 Hive Systems Password Table Is Here - Passwords Are Easier to Crack Than Ever
As you can see from the chart, if you create a unique, un-guessable password with upper and lower case letters plus numbers, an 11 digit password takes 41 years to crack. Add one more digit, and it takes millennia. Anything beyond that offers no additional protection because it is not meaningful within the span of your lifetime.
Shorter passwords are less likely to be forgotten and are quicker to type in (you will be typing your master password into Bitwarden a lot). There really is no reason to create an unnecessarily long password.
And if you want to try a Brute Force Calculator to see how long it will take to crack a password of different characters, try here:
I’d always recommend letting Bitwarden generate a strong, complex password when you don’t need to memorise it. Where you need to remember a strong, unique password, go for several random words. Much easier to remember than something containing upper- and lower-case letters, numbers and “special characters” and, depending on the number and length of the words you go for, just as secure (if not more so).
İs Bitwarden’s passphrase generator truly random and strong?
It is, but like all dictionary-based generators, it has limitations.
In addition to what @danmullen recommends above, I suggest creating your own passphrase so that you can combine the entropy of a random password with the memorability of a passphrase.
For example, use something memorable only to you:
<first-girlfirends-name>#<year>#<city> ==> AnnaC#1987#Denver
A dictionary-based attack won’t work on this, so it has to be brute forced. The password is only 17 characters, but it contains upper case letters, lower case letters, numbers, and symbols, so it will take 93 trillion years to crack.
So creating my own passphrase is more secure than the any other passphrase generator, okey got it. Plenty of thanks to all of you, I definitely got my answers.
thanks a lot again.
I wouldn’t say it’s more secure, but probably more memorable. That said, be careful using information that’s personal to you. Using the names of your four brothers and sisters isn’t going to be as difficult to guess as four completely random words 
Random words which you have chosen will be stronger than something a program generates (assuming you choose truly random words). The issue with having a program generate it is that it uses a defined dictionary and so the bad guys have access to the same dictionary and thus it is a relatively easy dictionary attack to try to crack your master password. You could of course use bitwarden to generate a pass phrase and then add something random to it.
As for strength it does not need to be very high. Looking at the weak points, the first is doing a bad thing like reusing a password as your master password. The next is your device where malware can capture your master password, or the unencrypted database. Third would be a flaw in the code which allows the database to be accessed. All of these are not dependent on your password strength.
Using a defined dictionary of just 8,000 words and generating a random passphrase consisting of 5 words, you could give an attacker the dictionary and it would still take years to crack.
Humans are actually really bad at choosing random things. A good compromise is using something like Diceware to generate random words for you.
I believe there is a common misconception out there that a password MUST be random or have some random element in it to be secure. In truth, it only has to constructed so that it is not guessable - a random component ensures this, but it isn’t the only way. Any method that ensures a hacker must brute force your password (i.e., because it cannot be guessed) is fine. That’s why I think a combination of words in a phrase that are meaningful only to you (i.e., can’t be guessed) mixed with some capitals, some special characters, and some numbers are the absolute best choice. Because they are shorter than random passphrases of equal entropy, they are both easier to type in and more memorable.
Having said this, if you want to generate strong passphrases for passwords other than your master password in Bitwarden, say to secure website logins or such that you MIGHT need to type in at some point, I totally agree that using random words from a Diceware dictionary is a very good option.
Essentially, you’re correct. However, it’s all too common for people to choose words that are seemingly difficult to guess, only to find that someone has cracked it because the information can be linked to them in some way. I generally find it’s far easier to just advise people to use truly random words rather than risk them choosing something bad!