Do you always update all of these accounts on the same day (or within a 2-week period)? If not, some of the old passwords could get erased earlier than expected (i.e., after less than a month) if the feature is implemented the way that you have requested it.
It sounds like perhaps a better solution would be an option to restrict the password history list to store only a single password at a time.
It turns out that there is a little-known bug in the password history implementation that can be exploited to achieve just this functionality. For each vault item where you want to limit the size of the password history to only N entries (N = 0–4), edit the item and create a specific number (M) of custom fields of the hidden type, where M = 6–N (e.g., in your case, to keep only one password in the password history, create five such hidden custom fields).
Each of the hidden custom fields created for this purpose should be given the same field name, but a unique field value. For example, in the example below, the field name has been set to pwpurge for all five fields, and the field values are set to 1, 2, 3, 4, and 5, respectively:
Save the edited item after you have added these fields.
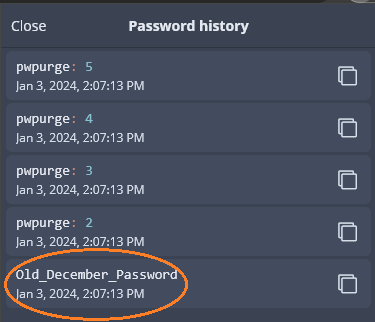
Now, each time that you change the password of the item, the password history will contain only the most recent value of the password, as shown below:
The caveats with this method are that it will stop working if Bitwarden fixes the bug, and that the password history (i.e., the one most recently used old password) will be lost if you ever edit and save the vault item without updating the password (e.g., if you are editing some other information stored in the item).