Summary
As a user of Bitwarden Send, I would like the Bitwarden Send page to display a hash of the resulting file (such as a SHA256) on the download page so that the receiving user can validate the hash before downloading the intended file.
At the moment, what’s usefull or reasuring on the recievers ends is that he can see the sender’s email (if they permit it).
Additionnaly, as the sender, I can compare the hash on the download page and the one calculated on my own device and validate that they match.
Description
The ability to verify the integrity and authenticity of a file is crucial for many users, particularly when handling sensitive information. By displaying a file hash (e.g., SHA256) on the Send download page, Bitwarden can provide an additional layer of security and trust for users exchanging files through the Send feature.
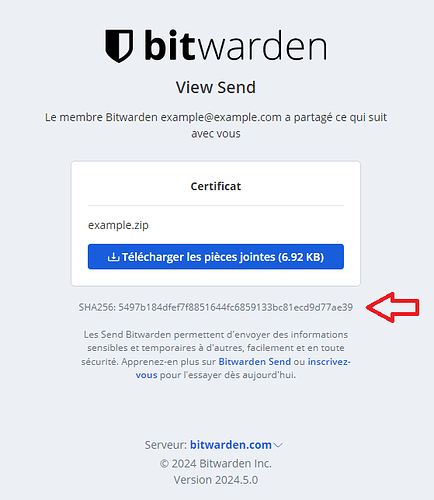
It cloud just be like this:
Use Case
- Scenario: A user sends a file through Bitwarden Send.
- Action: The receiving user opens the Send link.
- Result: The Send page displays a hash (such as SHA256) of the file.
- Benefit: The receiving user can validate the hash against the file they receive, ensuring the file has not been tampered with and is indeed the intended file.
Proposed Solution
- Generate Hash: Calculate a SHA256 (or other specified hash algorithm) of the file on the sender’s device.
- Display Hash: Show the calculated hash prominently on the Send download page, along with the email and with instructions on how to verify the hash.
- Optional: Provide a link or instructions to popular hash verification tools for user convenience (sush as 7zip).
Benefits
- Security: Enhances the security and trustworthiness of file transfers by allowing users to verify file integrity.
- Transparency: Provides transparency and reassurance for users receiving files, knowing they can confirm the file’s authenticity.
- User Trust: Builds user trust in Bitwarden’s commitment to security and user privacy.