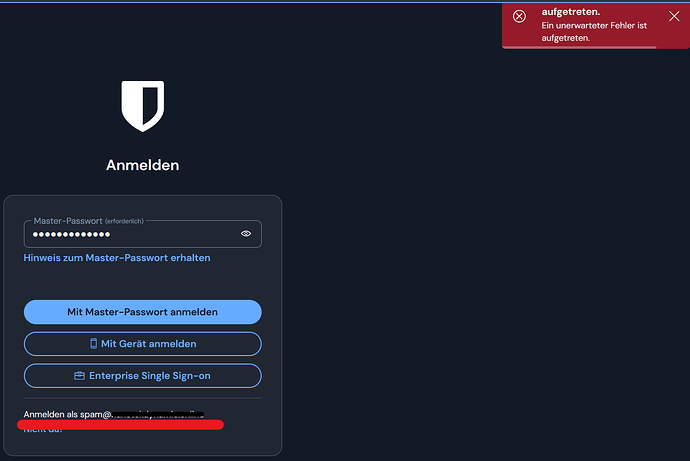
Some of the devs, please check the following. There might be a reproducable bug with the 2FA function on selfhosted servers (EU).
My server is running on a lxc proxmox (unprivileged) and after setting it up, I used the following commands
sudo su
apt-get update && apt-get upgrade -y && apt-get autoremove && apt-get autoclean
timedatectl set-timezone Europe/Berlin
## add repository ##
apt install software-properties-common -y
add-apt-repository universe -y
## install curl ##
apt-get install curl lsb-release -y
## install docker ##
apt install apt-transport-https ca-certificates curl software-properties-common -y
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo gpg --dearmor -o /usr/share/keyrings/docker-archive-keyring.gpg
echo "deb [arch=$(dpkg --print-architecture) signed-by=/usr/share/keyrings/docker-archive-keyring.gpg] https://download.docker.com/linux/ubuntu $(lsb_release -cs) stable" | sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
apt update
apt install docker-ce docker-ce-cli containerd.io -y
systemctl start docker
systemctl enable docker
systemctl status docker
## prepare bitwarden ##
adduser bitwarden
passwd bitwarden
groupadd docker
usermod -aG docker bitwarden
mkdir /opt/bitwarden
cd /opt/bitwarden
su bitwarden
sudo chmod -R 700 /opt/bitwarden
sudo chown -R bitwarden:bitwarden /opt/bitwarden
## install bitwarden ##
curl -Lso bitwarden.sh "https://func.bitwarden.com/api/dl/?app=self-host&platform=linux" && chmod 700 bitwarden.sh
./bitwarden.sh install
nano ./bwdata/env/global.override.env
./bitwarden.sh rebuild
./bitwarden.sh restart
./bitwarden.sh start
docker ps
Bitwarden is behind a nginx Proxy Manager with following settings:
http forwarding to port 80 with Force SSL with Lets Encrypt and HTTP/2
fyi: HSTS is not working for me because the admin-page will not load.
Bitwarden (EU) was installed without certificates, npm with Lets Encrypt is in front of Bitwarden.
- Create new account with an email address that is also registered at bitwarden.eu and that has a family plan subscription (system@…)
- After login and mail confirmation, I created an organization (same name as on bitwarden.eu)
- I loaded the family plan (json file)
- Creating new accounts on the self hosted server (with mails that are also registered at bitwarden.eu)
- adding them to the organization
- Now one account gets 2FA activated with TOTP, the other account not
Result: I cannot longer login into the 2FA protected account because there is no field for entering the TOTP. Instead there is an error:
I didn’t change anything in the yml-file because I got problems the first time with nginx Proxy Manager:
#
# Note: After making changes to this file you need to run the `rebuild` or `update`
# command for them to be applied.
#
# Full URL for accessing the installation from a browser. (Required)
url: http://xxxx.online
#
# Auto-generate the `./docker/docker-compose.yml` config file.
# WARNING: Disabling generated config files can break future updates. You will be
# responsible for maintaining this config file.
# Template: https://github.com/bitwarden/server/blob/master/util/Setup/Templates/DockerCompose.hbs
generate_compose_config: true
#
# Auto-generate the `./nginx/default.conf` file.
# WARNING: Disabling generated config files can break future updates. You will be
# responsible for maintaining this config file.
# Template: https://github.com/bitwarden/server/blob/master/util/Setup/Templates/NginxConfig.hbs
generate_nginx_config: true
#
# Docker compose file port mapping for HTTP. Leave empty to remove the port mapping.
# Learn more: https://docs.docker.com/compose/compose-file/#ports
http_port: 80
#
# Docker compose file port mapping for HTTPS. Leave empty to remove the port mapping.
# Learn more: https://docs.docker.com/compose/compose-file/#ports
https_port: 443
#
# Configure Nginx for Captcha.
captcha: false
#
# Configure Nginx for SSL.
ssl: false
#
# SSL versions used by Nginx (ssl_protocols). Leave empty for recommended default.
# Learn more: https://wiki.mozilla.org/Security/Server_Side_TLS
ssl_versions:
#
# SSL ciphersuites used by Nginx (ssl_ciphers). Leave empty for recommended default.
# Learn more: https://wiki.mozilla.org/Security/Server_Side_TLS
ssl_ciphersuites:
#
# Installation uses a managed Let's Encrypt certificate.
ssl_managed_lets_encrypt: false
#
# The actual certificate. (Required if using SSL without managed Let's Encrypt)
# Note: Path uses the container's ssl directory. The `./ssl` host directory is mapped to
# `/etc/ssl` within the container.
ssl_certificate_path:
#
# The certificate's private key. (Required if using SSL without managed Let's Encrypt)
# Note: Path uses the container's ssl directory. The `./ssl` host directory is mapped to
# `/etc/ssl` within the container.
ssl_key_path:
#
# If the certificate is trusted by a CA, you should provide the CA's certificate.
# Note: Path uses the container's ssl directory. The `./ssl` host directory is mapped to
# `/etc/ssl` within the container.
ssl_ca_path:
#
# Diffie Hellman ephemeral parameters
# Learn more: https://security.stackexchange.com/q/94390/79072
# Note: Path uses the container's ssl directory. The `./ssl` host directory is mapped to
# `/etc/ssl` within the container.
ssl_diffie_hellman_path:
#
# Nginx Header Content-Security-Policy parameter
# WARNING: Reconfiguring this parameter may break features. By changing this parameter
# you become responsible for maintaining this value.
nginx_header_content_security_policy:
#
# Communicate with the Bitwarden push relay service (push.bitwarden.com) for mobile
# app live sync.
push_notifications: true
#
# Use a docker volume (`mssql_data`) instead of a host-mapped volume for the persisted database.
# WARNING: Changing this value will cause you to lose access to the existing persisted database.
# Learn more: https://docs.docker.com/storage/volumes/
database_docker_volume: false
#
# Defines "real" IPs in nginx.conf. Useful for defining proxy servers that forward the
# client IP address.
# Learn more: https://nginx.org/en/docs/http/ngx_http_realip_module.html
#
# Defined as a dictionary, e.g.:
# real_ips: ['10.10.0.0/24', '172.16.0.0/16']
real_ips:
#
# Enable Key Connector (https://bitwarden.com/help/article/deploy-key-connector)
enable_key_connector: false
#
# Enable SCIM
enable_scim: false
I tried especially the SSL and real_ips section without success.
But that cant be a problem with the 2FA TOTP function, right?
This error is only for the account spam with activated 2FA.
I could reproduce this behavior every time and “crashed” 3 instances today. I had the problem since 2 days and restarted the container, restarted docker and rebuild Bitwarden without luck. Its definitely the 2FA and/or the combination of my setup.
Addition 1:
And its not only the browser but also the browser plugin and the app on Android. Disabling adblockers and privacy badger didn’t work in Firefox. Other browers will also fail. So its not a client problem
Addition 2:
As long as you stay logged in in the app or desktop client, you can sync with the server (lol). But if you must relogin, it will fail.
Addition 3:
I created another user (spam2@…) with mail 2FA.
Relogin fails with the same error message (see image above) but i got an email with my access code.
So it seems that Bitwarden didn’t want to load a page where the user can place the 2FA key. It’s not like a 404 or similiar. The page stays the same, only the error box in the upper right corner appears without context.