Can’t wait to see a breakdown from Bitwarden for all the palant.info’s “What’s in a PR statement” points detailing how the situation’s (hopefully) better for Bitwarden’s customers.
![]()
(suspect you’ll be waiting a long time - or see the biggest list of jargonistic buzzwords you’ve ever seen in your life!) ![]()
If it ends up with buzzwords, they’re bound to lose customers.
Thanks for the continued feedback all, let’s keep comments constructive, you can check out all the steps Bitwarden takes to protect user data here: https://bitwarden.com/compliance/
Okay, Mycenius.
Yes - but hopefully it genuinely doesn’t come to that - I’m afraid I’m a cynic to a degree when it comes to businesses/corporations taking ownership of their responsibilities. But if I was one of the affected customers I would be changing all my passwords as quickly as I can, starting with the most critical, and where possible the email address I used for that account as well.
Someone else posted somewhere (I can’t recall if it was a post here or elsewhere), and to paraphrase, ‘they felt sorry for the LP staff of last few years having to continually fight fires and deal with issues’ - I sympathise with that as I have worked in (albeit non-InfoSec/Tech) environments where its been a bit like that due to poor decisions by a business having long-term ramifications for the staff and team. Hopefully they can turn it around with some positive changes there (otherwise all 33 million people who use the service trying to all migrate to other providers may have unforeseen consequences, at least short term)? The good thing is BW (and 1PW for that matter) have a much more pro-active and integrity based approach which is reassuring - and I think fairly well proven to date - so as has been pointed out some of the things that have happened elsewhere can’t or or almost certainly shouldn’t happen with BW.
Good reminder @bw-admin, was drifting a bit off tangent there… ![]() Back on track something I was curious on was how to verify BW iterations for your own vault - obviously this has become a huge issue with the LP Incident; and some may find it reassuring to see the value somewhere showing the iterations actually being applied? Given a lot of LP accounts look like they were only on 1 or 500, and many only 5,000 not their 100,100 level that LP stated - I think it would be good (if it’s not already there) if this was visible; even just an ‘info’ field on main (general) account settings showing what the current value is (and showing the one being actually ‘used’ for the vaults, rather than just an arbitrary system wide policy setting or statement)?
Back on track something I was curious on was how to verify BW iterations for your own vault - obviously this has become a huge issue with the LP Incident; and some may find it reassuring to see the value somewhere showing the iterations actually being applied? Given a lot of LP accounts look like they were only on 1 or 500, and many only 5,000 not their 100,100 level that LP stated - I think it would be good (if it’s not already there) if this was visible; even just an ‘info’ field on main (general) account settings showing what the current value is (and showing the one being actually ‘used’ for the vaults, rather than just an arbitrary system wide policy setting or statement)?
Someone asked about it in another thread (on this forum I think?) - they were saying about you could ‘choose’ your iterations setting in Bitwarden like LP does? Is that correct as I couldn’t find help documentation that specifically says that - or if it exists is it a setting only accessible with a premium account¹, or that only shows if you rotate your key or something? I think one lesson from LP is the fact (a) the setting was in an obscure place that many users weren’t aware of and never checked, (b) users who did know about it could set it to a setting lower than the 100,001 default, and (c) there was no security warning if you did manually set it lower than the default…
If it’s not present is that something BW would put on the roadmap for future to give users/customers visibility?
(¹ I’m still running a free version of BW to trial it as I haven’t quite pulled the lever to ‘jump ship’ from 1PW yet - so was wondering if it’s there but not showing because I’m on the free account?)
Thanks @Mycenius, the setting is currently viewable by visiting the web vault, tapping your profile in the top right → Account Settings → Security → Keys and labelled as KDF Algorithm.
The feedback to make it more visible or include in help center documentation has been passed along to the team.
Thanks @bw-admin! I knew I had seen it somewhere - for some reason I didn’t see it on that tab when I relooked this morning.
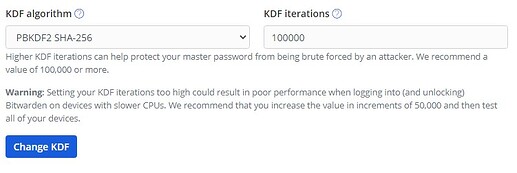
I see it allows you to go as low as 1 in the iterations field (see below screenshot - although I haven’t clicked the “Change KDF” button so don’t know if that gives a warning or rejects that low a setting) - In light of the LP issues should this be restricted to some level, e.g. can’t go below 50,000 or even 100,000 or at least you have to jump through hoops to do so (re-enter master password, etc)? I realise there is an additional 100,000 for the vaults stored on the server so even on 1 there is nominally 100,001 server side (rather than 200,001), but setting 1 would still leave it vulnerable client side and while in transit between the two, right?
Also as an aside, all the documentation says 100,001 iterations, yet my default settings show 100,000 (see below) - am I missing something obvious about the additional “1” iteration?
It allows any value in the range 5,000-2,000,000. It has been argued that these limits are too low.
The 100,000 client-side iterations are to calculate the Master Key. Then there is one more client-side round of PBKDF2-SHA256 to hash the Master Key, which generates the Master Password Hash that is transmitted to the servers. This is explained in the security white paper, which you’ll enjoy reading.
As I’ve pointed out elsewhere, only the initial (100,000) iterations for computing the Master Key must be performed by someone attempting to crack your master password, so the extra 100,001 iterations are not so relevant for vault security (they serve other purposes).
Thanks as always @grb! I guess my last comments on this would be:
Yes - I’d have thought so - at least the low value should be much higher based on my reading and steep learning in last couple of weeks; and details of the LP implementation and the (process/user setting) weaknesses it’s exposed post their incident…?
Thanks yes - I am partly though reading! ![]()
![]() (actually am reading both the BW & 1PW ones at present) - very dry, and a bit slow going, but still informative!
(actually am reading both the BW & 1PW ones at present) - very dry, and a bit slow going, but still informative!
![]()
Re the iterations, I have been with Bitwarden when they were still a beta service created and maintained by one guy. I believe (but am not sure) that the number was then 500 and it wasn’t updated automatically - so I upped the value.
I drifted away for a few years to a competitor and when I came back, I saw that Bitwarden now recommended (I think) 100,000 so I increased it again. After the LP breach I actually increased it all the way to the current maximum (2 million) without any lag or issues.
I wish BW were a little more proactive in warning against a low value, and I agree with others here that the minimum should definitely be increased to 200,000 or more.
Side note: BW was really rough around the edges then with no stand alone desktop app and a very basic Android app. I think it only worked on Chrome then. The dev was very involved and responsive though so it improved rapidly. Ahhh, memories…
…what, you’re not enjoying the adventures of Oscar, Alice, and Molly?
I just set my iterations to 1,000,000. No slowness on my MacBook Air M1, Mac Studio, Windows 11 laptop (Dell Inspiron 7 something), or iPhone 14 Pro. Think I’m done for a few years messing with it now. ![]()
Just to add one point to these discussions about how much of the vault is actually encrypted. It seems to me that Password Managers have been slow to realise that there is much of value to a bad guy if URLs and Names (not usernames) Notes, etc. are in the clear. At the very least, examination of this data will provide a shortlist of the best prizes to expend effort in cracking. For me, this was the awful moment when reading about the Lastpass debacle. The bad guy will know where I bank, where my savings are, what commercial relationships I have. Even if the bad guy doesn’t know my login credentials, knowledge is still power.
Hi @Basjoe, afraid its not really a case of realising, its a deliberate choice by the Password Managers concerned that do it. Bitwarden (& 1Password and NordPass) don’t do this - they encrypt everything. LastPass deliberately and consciously chose not to do it (and from what I have read have repeatedly ignored requests and pleas from Infosec experts and bloggers to start doing it; and that’s been going on for many years now - at least since 2015). It’s well know what benefits bad actors can get from this data and it’s been well documented for many years too.
So why not encrypt it? Because if they encrypt it they can’t read it - they wanted your meta data (to analyse; and quite possibly to sell for extra revenue as analytics). Not encrypting this data is a very deliberate choice by these companies, not an oversight or just being a bit ‘slow on the uptake’… They want to be able to read it and harvest & analyse it, and have the potential to sell it… It’s good business for them revenue wise (I have seen one article that stated there is good evidence LP wasn’t just using this data internally and were selling, albeit anonymised, analytics data about its customers web activity - but this isn’t 100% verified AFAIK and don’t know if it can ever be proven for sure - or verified it didn’t happen either).
Good thing is there are some good companies that take security extremely seriously and have high integrity - BW included. So that’s not an issue here.
Re fact that LP are not encrypting the URL. It has to be deliberate and your comment is the only reason I can think of.
LastPass reportedly won’t encrypt the url in order to increase workflow efficiency for its browser extension autofill. This is a conscious choice to prioritize features and ease of use over security. A constant tension with password managers and we can see where LP sits in that argument. The issue is that most people don’t know this and they wouldn’t want their mom or wife seeing those URLs. The data breach may not expose people’s password data where they had strong passwords and a high iteration set but it could still expose them in uncomfortable ways.
Does anyone know if Bitwarden exposes our email address that we use to sign in? I assume that’s not encrypted but curious.
I understand the current recommended industry standard is 310,000.