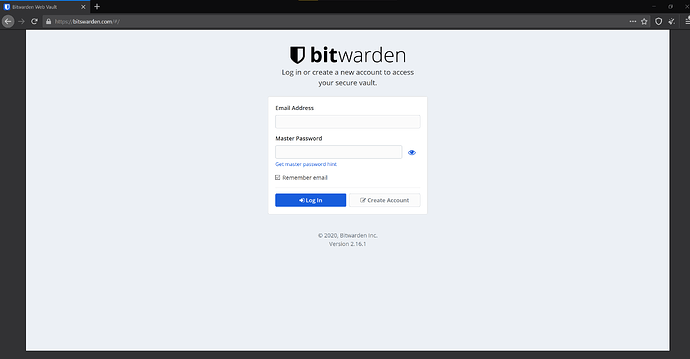
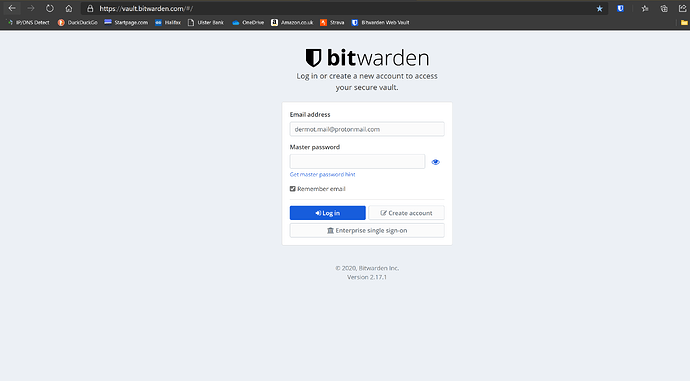
I attach two images, one of the official vault and the other, the hosted version which fooled me, given it was in the top results on Bing and DuckDuckGo yesterday. I clicked on it thinking it was the most direct link to the vault. I guess I was a bit careless, but should a self-hosted instance have a near identical URL and almost identical appearance? I can’t get my head around the idea that this person thought it was a good idea to host his own instance on a URL nearly identical to the official one. I would wonder if he might get a visit from the FBI! I think it was a very poor judgement, especially for someone who was technically capable of doing so, and with a product that is VERY security sensitive. It has cost me at least 8 hours of computer work to change all my passwords and reset all 2FA settings, as well as cancelling all my credit and debit cards, and all the stress and anxiety.
Another option to prevent phishing attempts would be to use only the extension and save the password of bitwarden web vault in it and URL as https://vault.bitwarden.com/#/ and URL type as exact and first login with extension and then filling it to the web vault.
Do you mean you should save the authentic Bitwarden web vault URL in your bookmarks? That’s what I’ve done. I visited Bitwarden.com, clicked DOWNLOAD, then clicked on the ‘Access Web Vault’ tab. I then bookmarked that in my cloud-saved Microsoft Edge bookmarks. Actually I think I know what you mean… Does the extension stop you filling in the details for a fake vault site IF the URL is not exact, or does it merely not show in the extension when you open it on the fake site? Please clarify what you mean precisely.
Warning:This can lock you out of your account is you do not memorize the password.
I mean to save Bitwarden’s Password in Bitwarden itself so that it will autofill for you.
Exact URL is needed because it should not fill in any other any other website.
You can just save some random password in bitwarden for vault.bitwarden.com
If you don’t see the popup with the number for the site on the extension, then stay away from the site as it is fake.
I think now bitswarden cannot be accessed. But I was never ever able to reproduce the same behaviour in any of such websites. Always I get the username or password is incorrect.(with fake email). Can you please confirm wheter you saw the vault inside. Maybe you were in a panic and could not remember whether you saw it or not.
But I could not reproduce the same behaviour in any of such sites. @Merlin7
We need something that verifies a user is at the correct Bitwarden web portal. I have no idea what solutions exist if any but we need something to differentiate the legit site from the self-hosted ones.
This does make me happy I salt my important passwords!
Other than the URL there should be some visual thing like an icon or colour for the self hosted version.
A different color or an icon cannot be the solution as Bitwarden is open source and therefore a self-hosted version could easily be adjusted to look like the main website. It needs something different.
Ideas anyone?
Some websites ask user to choose a picture during registration and will display it when user enter their username
Pretty good idea, that would help
Is there a way to do what LessPass does, where you enter the master password it changes the icons? https://lesspass.com/#/
I think doing it at the username would be more effective, I don’t want to enter my master password on the wrong site.
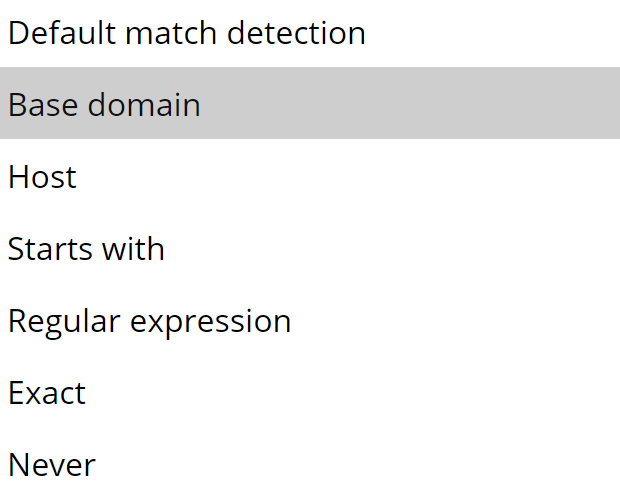
Should I choose EXACT if I want to set that up?
(EDIT: I’ve set up an entry for fake Bitwarden login credentials, so I can use that to verify before inputting my real Bitwarden password from memory.)
@sugianto That’s a great idea.
@anon13423310 Yes that’s what happened - I entered my correct login credentials and got an ‘error - wrong password’ warning. I could not understand how this could happen, first I thought ‘‘WHAT? I can’t be locked out?’’, then I looked up and saw bitSwarden and went into panic mdoe. So I never got to log-in. With the mist of panic afterwards, I couldn’t remember if I got logged in or not, but it’s clearer now that I have calmed down.
@dangostylver What is lesspass, it is a Bitwarden derivative? They use their logo on that page.
Yes that is the EXACT I talked about. You’d better follow vachan’s advice about storing the password.
If you did not login to the fake website then there was no need to change all passwords. Just change your master password with rotate encryption key (Just in Case) and reset 2FA for bitwarden.
Anyway what you did was correct though.
Thanks! I didn’t feel comfortable putting my real Bitwarden password as a real entry so created a fake credentials entry with EXACT selected. I was OK with changing everything even though it was a lot of work. My fear was that the fake login page had collected my login credentials, including the 2FA code, and may have logged in in real time to my vault. That would be a very sophisticated scam. I don’t know if it’s technically possible?
As a side issue, I was able to lock one of my cards, but the others were cancelled. If I’d had the mobile banking apps for those cards installed, I could have temporarily frozen the cards until the dust settled.
Your 2FA code changes every 30 second if you are using an authenticator app.
So there is nothing that a person can do with your previous code.
1. Allow users to enter the email first separately.
2. If the email entered is not on the self hosted server then display an error message. Block the user from entering the Master Password.
Hello,
I got a recommendation against misspelling the site. If you bookmark it and go always through that link it will eliminate this kind of problem (that’s how I do it  ).
).
I still can’t believe a person would use the domain bitswarden for self hosting. It just doesn’t make sense, why would a person even do this?